Systematic, consistent and traceable cybersecurity risk analysis: TARA-based assessments for complex systems
CYMETRIS is a revolutionary platform for assessing cybersecurity risks in the development of technical systems. Tailored to the needs of cybersecurity engineers, it supports traceable, dynamic and standards-compliant assessments throughout the product lifecycle - from development and operation to decommissioning.
By integrating the principles of TARA (Threat Analysis and Risk Assessment), CYMETRIS combines methodological accuracy with practical applicability. The result: a sound risk analysis that enables reliable decisions when selecting cybersecurity measures for a product developed.
The CYMETRIS approach provides consistency, visual clarity and improved collaboration between engineering, compliance and supply chain stakeholders. Whether you are validating system architectures, adapting to new threats or complying with industry regulations such as ISO/SAE 21434 and UN R155, CYMETRIS provides the analytical foundation, collaborative workflows and technical transparency your cybersecurity process needs.
CYMETRIS ensures that all elements of the cybersecurity risk analysis — assets, assumptions, threats, vulnerabilities, and mitigations — are logically and structurally consistent. It applies a rule-based logic aligned with industry-specific approaches (like ISO/SAE 21434) to perform automated plausibility checks during data input and modification.
Broken logic chains, contradictory threat vectors, or incomplete documentation are flagged in real-time. This helps prevent flawed analysis structures and enforces high methodological quality from the beginning.
This core feature not only reduces the risk of human error but also accelerates the assessment process. It ensures a reliable analytical foundation for complex product systems, where interdependencies across components and domains are the norm.
Collaboration across Supply Chain (Guided Demo)

Unlike static risk reports, CYMETRIS enables dynamic, iterative risk analysis. Whenever your product architecture evolves — through added components, updated threat intelligence, or new regulations — the system allows you to update your risk model accordingly.
Assumptions, likelihoods, risk levels, and mitigation effectiveness are transparently versioned and carried forward across each iteration. This creates a living document that reflects the real-world risk landscape as it changes.
Interactive dashboards visualize trends over time and expose maturity gaps in implemented controls. As a result, engineering teams and project leaders can make informed decisions at every stage of the lifecycle — from early concept to end-of-life.
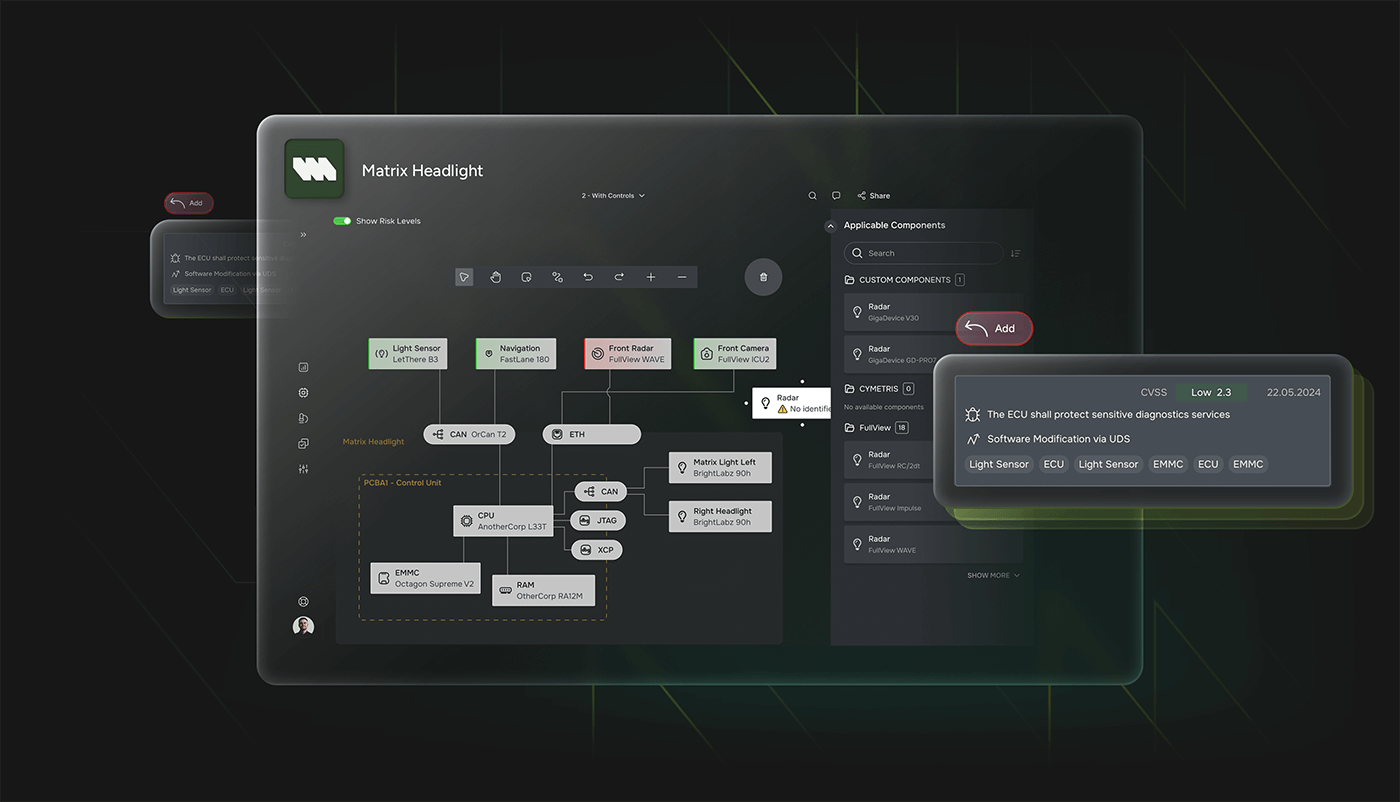
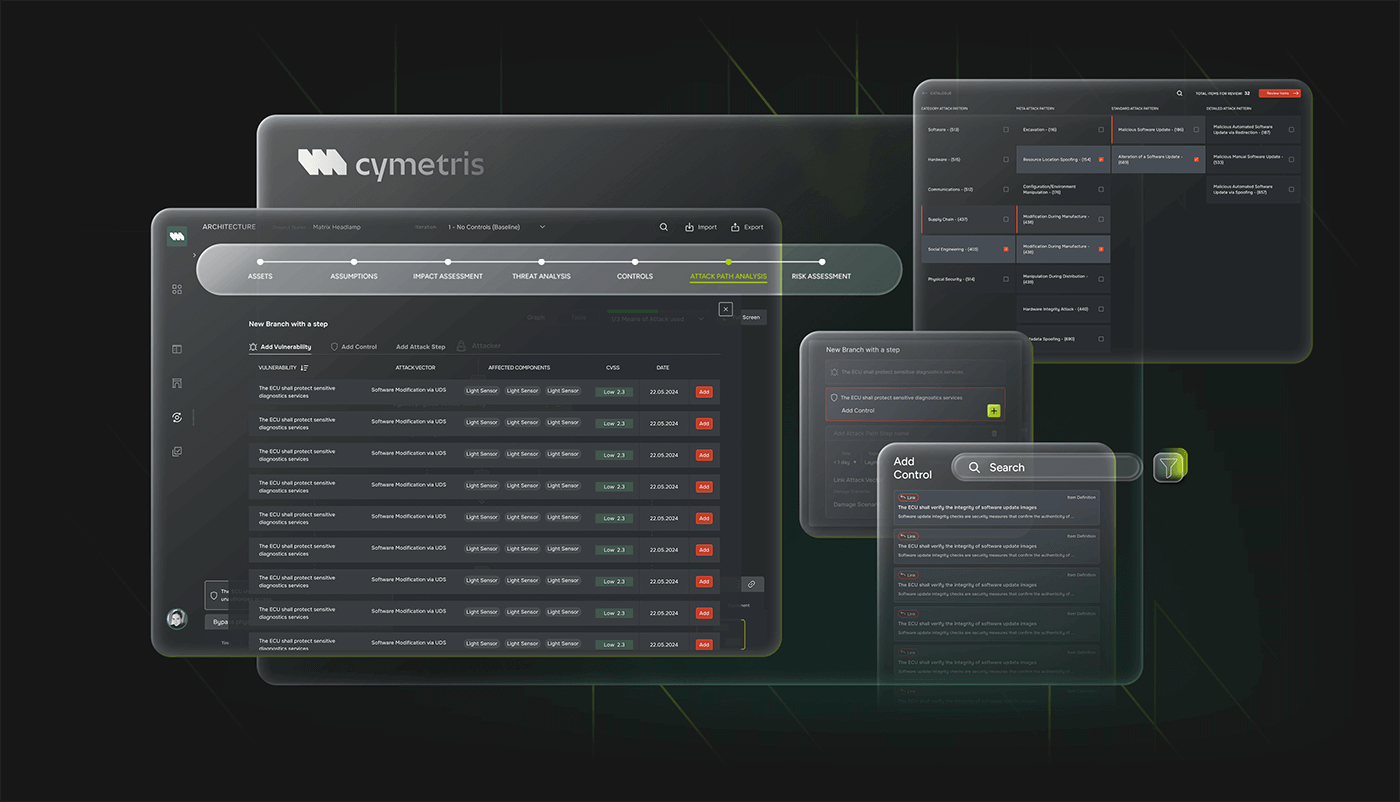
CYMETRIS allows users to explore potential attack vectors through a visual, graph-based interface. Each attack path is represented in terms of linked assets, vulnerabilities, threats, and countermeasures — all from the attacker's point of view.
The visualization highlights redundant paths, high-risk nodes, and dependencies that might be overlooked in text-based models. Users can interact with the graph to run simulations, test hypotheses, and evaluate different mitigation strategies.
This approach helps security engineers not just to identify risks, but to understand them in context — driving more effective, risk-informed architectural decisions and enabling clear communication with non-technical stakeholders.

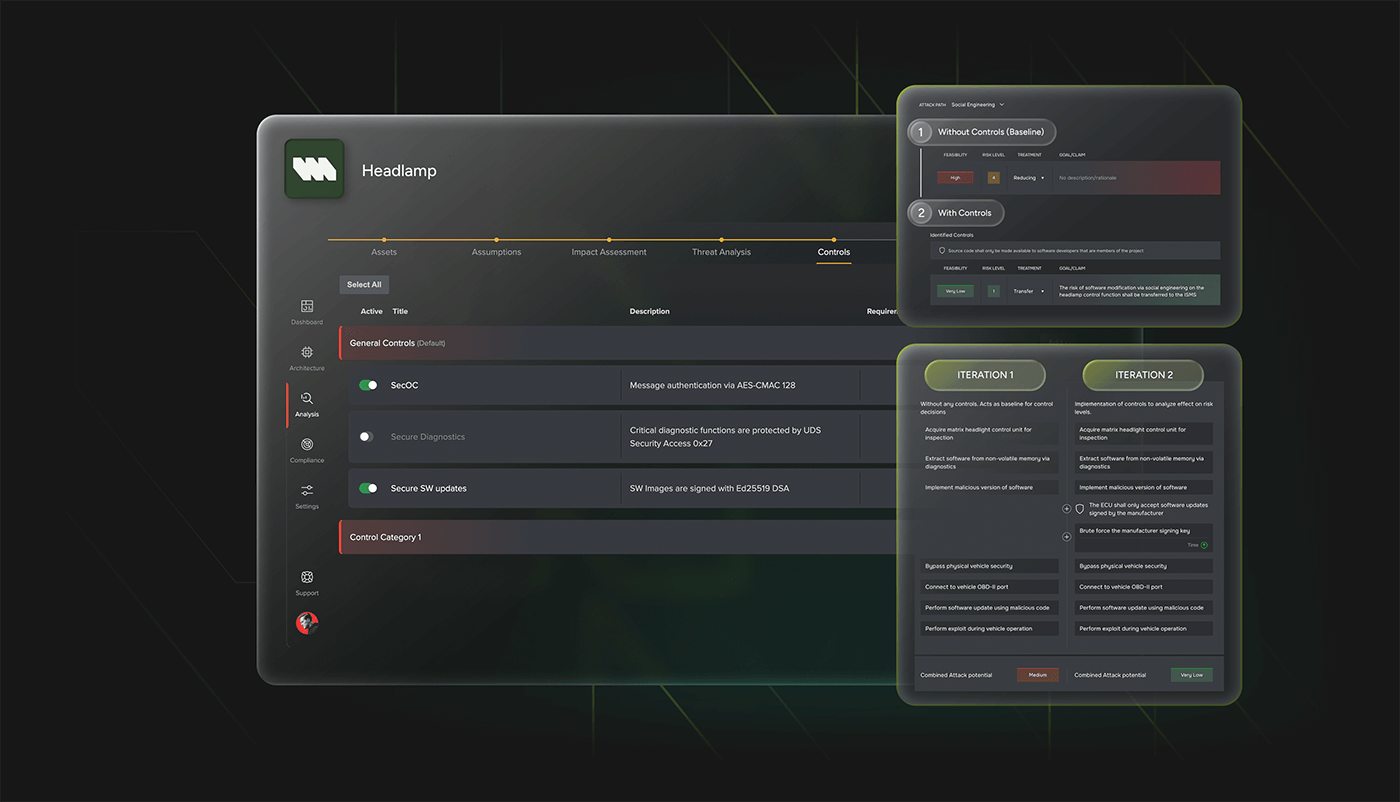
CYMETRIS enables fine-grained assignment of risks to specific parts of your system — whether logical modules, physical hardware, or functional processes. This mapping supports deeper traceability and more targeted risk response.
Rather than analyzing threats in isolation, the platform links them to real components and operational environments. That means users can analyze threats in the context of actual systems, not just theoretical models.
It’s especially powerful in projects where systems span multiple layers — such as embedded automotive controllers, industrial automation systems, or connected medical devices — where visibility and traceability across domains is essential.
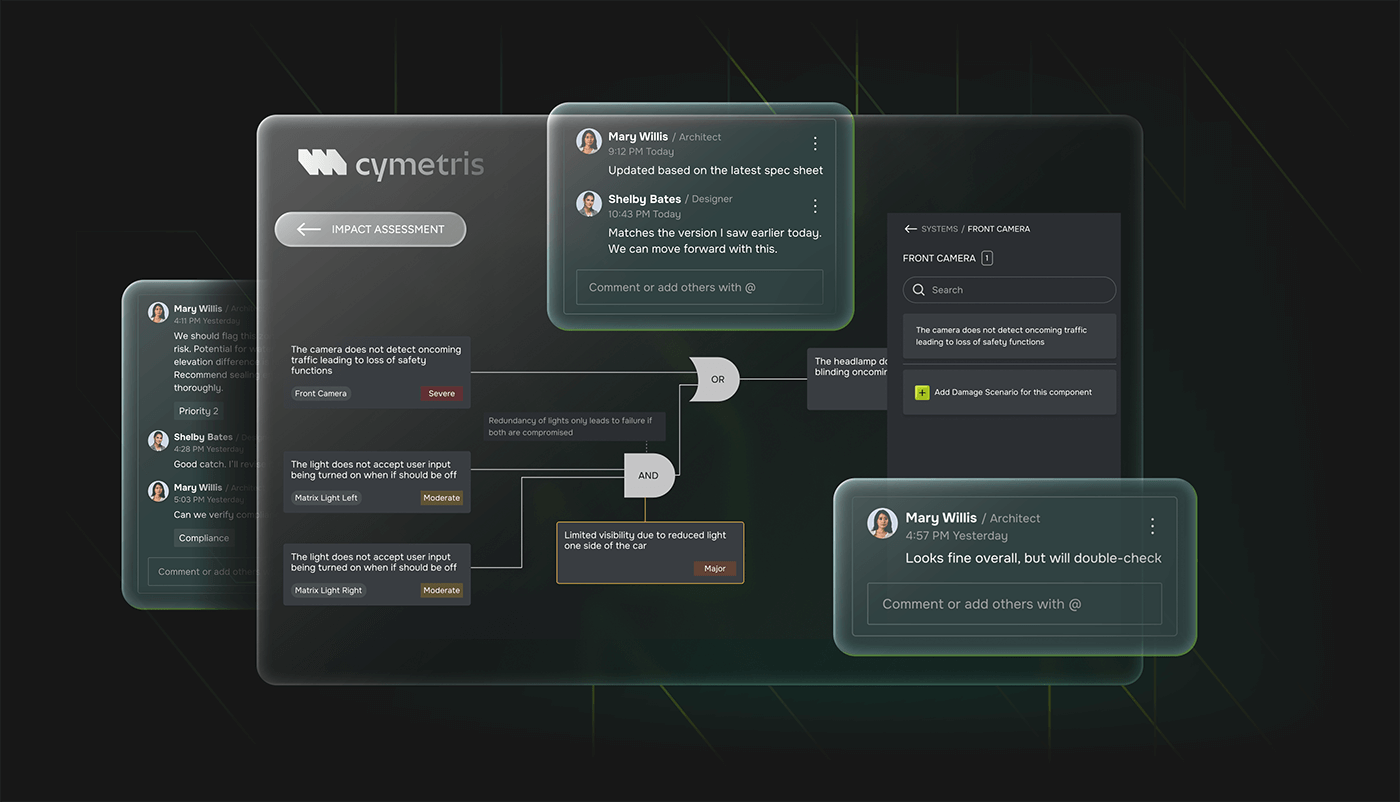
Cybersecurity is a cross-functional challenge. CYMETRIS supports collaboration by allowing multiple users — from in-house teams to suppliers — to work together within the same platform.
Access can be controlled by roles, ensuring each user sees only the relevant parts of the analysis. Context-based comments and review features help streamline feedback and documentation processes, without relying on external tools or disconnected workflows.
This collaborative model fosters shared understanding across disciplines, accelerates decision-making, and helps ensure cybersecurity considerations are embedded early and consistently throughout the development process.
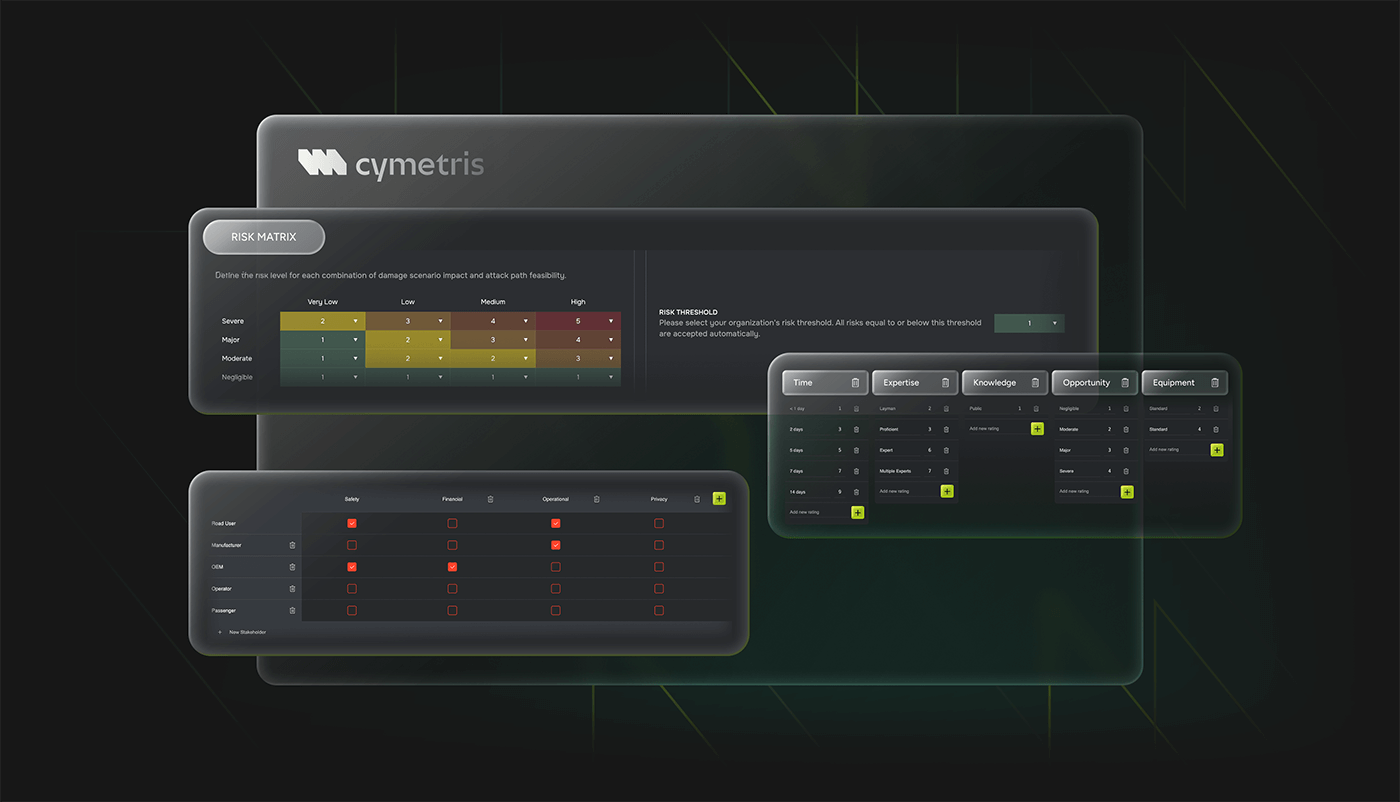
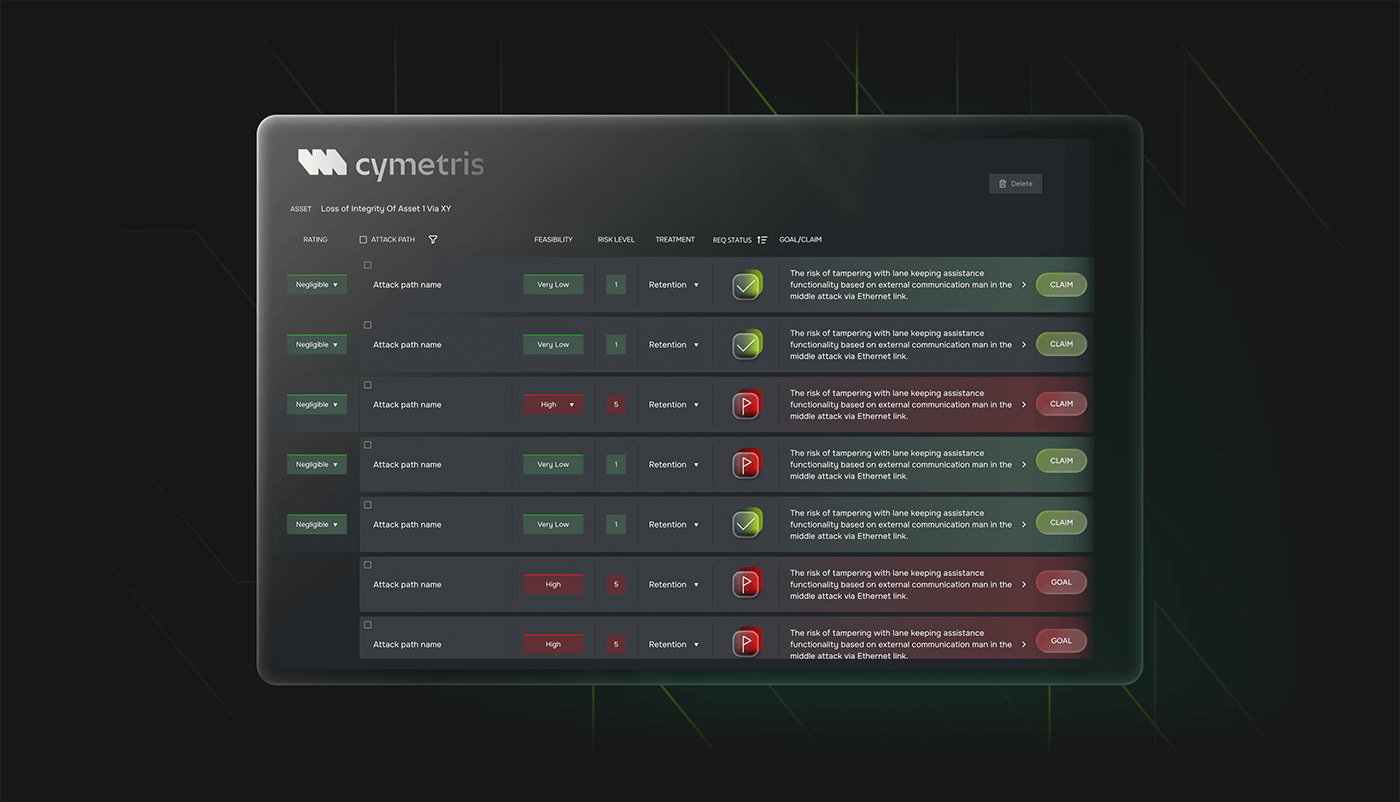
CYMETRIS includes a configurable risk matrix that aggregates threats, vulnerabilities, likelihoods, and potential impacts into a unified view. The matrix is fully traceable, updated in real-time, and embedded into the TARA process.
Users can apply both qualitative and quantitative scoring methods, simulate what-if scenarios, and instantly see how changes in the threat landscape affect the overall risk profile.
Because all inputs are linked to structured elements in the system model, the matrix becomes a powerful, living reflection of actual product risk — not just a compliance artifact, but a true decision-making tool.
CYMETRIS gives you full control over how your organization defines and applies cybersecurity risk assessments. Custom scoring scales, decision logic, control frameworks, and asset catalogs can be configured directly within the platform.
This flexibility enables engineering teams to use internal processes while still aligning with external standards. No-code customization means you can adapt parameters — like risk prioritization, feasibility, or severity — to your specific product and workflow needs.
As a result, companies can embed their internal governance and quality requirements into the tool — ensuring consistency, repeatability, and alignment across teams, projects, and domains.
CYMETRIS makes it easy to track and demonstrate compliance with key cybersecurity standards. For any industry, specific industrial standards and regulations, such as ISO/SAE 21434, UN R155, IEC 62443 and NIST 8259, can be fully integrated. This flexible approach is natively integrated into the platform.
A real-time compliance dashboard shows how current risk models map to regulatory requirements, flagging any gaps or deviations that need attention. Documentation and evidence for audits are generated automatically from analysis data.
This not only simplifies compliance — it also supports audit readiness and reduces the time and cost of proving conformity, especially in highly regulated industries.

CYMETRIS offers a robust and secure API for integrating with your existing systems — including PLM, ALM, MBSE, and requirements management platforms. This ensures data flows smoothly between tools without duplication or manual workarounds.
The API supports bidirectional communication, automated updates, and live synchronization of cybersecurity data. Risk findings can be linked to system requirements, visualized in engineering dashboards, or exported for reporting.
This integration capability ensures CYMETRIS becomes a connected part of your engineering ecosystem — supporting automation, reducing errors, and delivering real-time insight to stakeholders across the organization.
We'd be happy to show you how it works with a live demo. Let's discuss how we can integrate CYMETRIS into your existing tools and processes and how you can increase cybersecurity efficiency at organisational and project level.
At CYMETRIS, innovative concepts in the implementation of cybersecurity meet state-of-the-art software-based solutions in combination with modern AI technology.
Adding {{itemName}} to cart
Added {{itemName}} to cart